Security
Our platform is built by embedding security throughout the software development lifecycle. We follow rigorous operational security practices such as penetration testing, vulnerability assessments and strong internal access controls. We believe transparency is the key to winning trust — we publicly share how we operate and work closely with our customers and partners to address their security needs.
Organizational
Security begins on day one here, and we view it as everyone’s responsibility. All employees receive security, privacy, and compliance training the moment they start to keep both Stardog and customer data safe and secure. Our Information Security team provides the knowledge and skills needed to avoid or minimize security risks on an ongoing basis via our security training and awareness program.
This commitment to security extends to our executives. The Executive Leadership Team, a cross-functional group of executives spanning the enterprise, drives executive alignment across the organization and ensures that security awareness and initiatives permeate throughout the organization. Stardog screens all employees prior to hiring through third-party experts. Background screening includes criminal, education, employment, financial, and where applicable, drug screening.
Software Development Lifecycle
Stardog has a software development lifecycle (SDLC) that builds security into all steps, from feature requests to production monitoring, supported by tooling designed to trace a feature through the lifecycle. We have automatic security scanning of systems, libraries and code, and automated vulnerability tracking. All code is checked into a source control system that requires single sign-on with multifactor authentication, with granular permissions. Code merge requires approval from the functional engineering owners of each area impacted, and all code is peer reviewed.
We run quality checks (such as unit tests and end-to-end tests) at multiple stages of the SDLC process, including at code merge, after code merge, at release and in production. Our testing process includes unit and regression tests, integration tests across various platforms and systems, chaos, and other stress testing, as well as general performance benchmarking. Our SDLC process also requires updating and maintaining our comprehensive product documentation.
Business Continuity
We have established and maintain disaster recovery and business continuity plans so that the Stardog software is reliable and recoverable. We test for resiliency across our cloud providers and implement and test backup and restore procedures.
Vulnerability Assessments & Management
Detecting and quickly fixing vulnerable software is among the most important responsibilities for any software or service provider, whether the vulnerability exists in your code or the software that you rely on. We take this responsibility very seriously, and provide information about our remediation timelines in our Support Policy.
Network Security Monitoring
We implement proactive security procedures, such as perimeter defense and network intrusion prevention systems. Vulnerability assessments and penetration testing of the Stardog network infrastructure are also evaluated and conducted on a regular basis by both internal Stardog resources and third-party security professionals.
Vulnerability & Penetration testing
Internally we use several well-known security scanning tools to identify vulnerabilities within the platform. Stardog also employs third-party services to analyze our public-facing internet sites and identify potential risks. Severity-0 vulnerabilities, such as zero days that are known to be actively exploited, are treated with the highest urgency, and their fix is prioritized above all other rollouts
Additionally, we engage with third parties to perform penetration testing of our network infrastructure as well as our applications.
Incident Management
We have a formal security incident response plan in place. This involves all aspects of Stardog’s team including CloudOps, Development, Support, Legal, Finance, and Executives. Customers are asked to direct all security requests to support.stardog.com
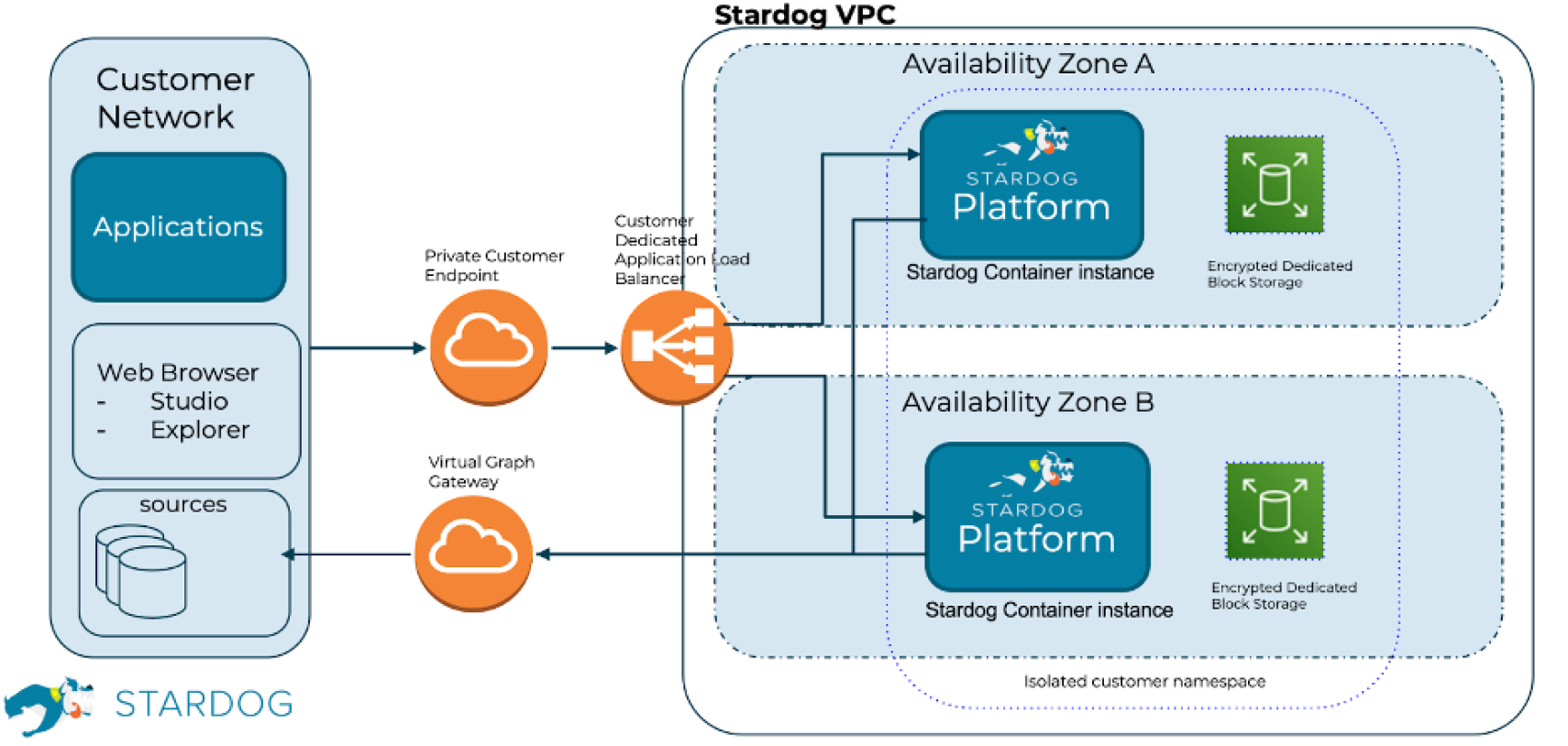
Cloud Architecture
Our cloud architecture is designed to segregate and restrict data access based on the customer and on the customer’s business needs. The architecture of the cloud environment used by Stardog provides logical data separation and role-based access privileges, all controlled on a customer-specific level. Production and testing environments are separated.
Data Encryption
Stardog implements encryption for data at rest using the Advanced Encryption Standard (AES) algorithm with a key size of 256 bits and Transport Layer Security (TLS) for data in transit.

